

Firms, or more generally, organizations, develop and become larger along time, using more and more computers to work. This growth in the number of computers leads to a growth of software use (operating systems and their applications, for example) and, as a result, to the growth in the number of software use/access licenses to be purchased and managed. For the owners of software intellectual property rights, this process leads to a greater supervision of users to regulate lawful access to software.The situation occurs when all of the software used by an organization is proprietary. This results in some costs — transaction costs — that are not usually taken into account by administrators and managers. What happens if FLOSS is used? We will show that this choice leads to a reduction in transaction costs in terms of computation costs and in terms of the number of managed contracts, which can be numerically reduced by half.
Contents
Introduction
From information systems to information infrastructures
Modes of interaction in computer network architectures
Transaction costs
Network examples
Conclusion
Introduction
This article is based on the theoretical studies of Ole Hanseth as well as the studies of Victor Prochnik, of the Economics Institute of Federal Univesity of Rio de Janeiro. Hanseth describes information infrastructures as a result of a process of management in time. He uses a biological metaphore — cultivation — to describe this process, instead of the idea of designing and implementing from scratch, which he calls "Big–Bang." Prochnik examines transaction costs of a contract: searching (the one to bargain with); writing (the contract); supervising (the fulfillment of the contract); and, demanding (when the terms of the contract are not being observed).
This paper will apply these ideas to the use of FLOSS networks, which helps to "set free" the cultivation of the information infrastructure of a firm by reducing its transaction costs. These costs are reduced because of the absence of access control mechanisms that are embedded in proprietary software.
From information systems to information infrastructures
Once upon a time, computers existed as stand–alone devices. There was no (or very little) communication between computers within an organization. All work was truly local, based on local needs and standards. As organizations grew, personnel and computers multiplied. Methodologies were developed to all inidividuals within organizations to communicate to reduce duplication of data and work, including models such as Structured Systems Analysis (Gane and Sarson, 1983); Modern Structured Analysis (Yourdan, 1990); Structured Systems Design (Page–Jones, 1988); and, most recently, UML — Unified Modeling Language (Booch, et al., 1999).
All these methodologies (and many others) have been used for at least twenty years, to model work and data to a certain size, time, and place. In the words of Hanseth (2002):
"in short: IS methodologies aim at developing a closed system by a closed project organization for a closed customer organization within a closed time frame."Planning information systems (IS) — by scratching, designing, implementing, specifying, and "big–banging" — becomes harder because it is not possible to change the installed base of hardware and software immediately. The solutions are: (1) to improve the installed base by adding new funcionalities; or, (2) to extend the installed base by adding new elements to it (Hanseth, 2002).
Information systems evolve into information infrastructures. Information infrastructures are defined as "a shared, evolving, open, standardized, and heterogeneous installed base" (Hanseth, 2002). Its extention or improvement depends strongly on the existing information infrastructure, that is, the installed base. Hence, we can see that our working definitions of "information infrastructure" and "installed base" depend on each other. Hanseth does not ignore information systems; they are treated in another way: as local phenomena.
Hanseth splits information infrastructures into two levels: application infrastructures and support infrastructures, wih the first at the top of the second. The support infrastruture is split into two categories: transport and service infrastructures. These levels are depicted in Figure 1.
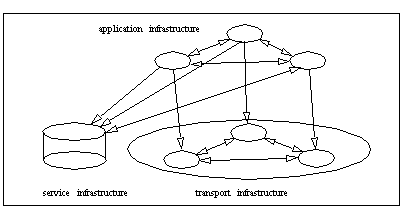 Figure 1: Information infrastructures (Hanseth, 2002).
Figure 1: Information infrastructures (Hanseth, 2002).
For example, Web browsers are part of the application infrastructure; TCP/IP is part of the transport infrastructure; and, DNS is part of the service infrastructure.
To escape from certain situations where an organization is "locked–in" to a certain software or hardware platform (Shapiro and Varian, 1999), Hanseth mentions the use of gateways, elements that "link different infrastructures which provide the same kind of service based on different protocols/standards. The infrastructures that are linked this way are called neighbouring infrastructures" (Hanseth, 2002). This situation is depicted below. One example of a gateway is Samba, which connects Windows and GNU/Linux infrastructures. This will be discussed later in this paper.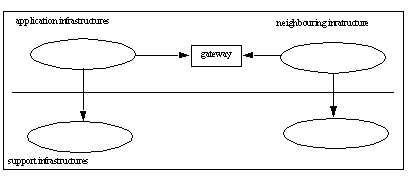
Figure 2: Ecologies of infrastructures (Hanseth, 2002).
In this paper we are interested in information infrastructures with up to 300 users and where an installed base depends strongly on proprietary software, contracts and licensing agreements, and associated costs.
We can describe simply the modes of computational interaction as client–server and peer–to–peer.
Client–server architecture
Servers handle requests for computational processing, acting as a locus for specific programs, data, and acting as a gateway to other networked resources. Clients send requests to the server for specific tasks; servers treat these requests in a centralized manner. See figure below:
In the case of this architecture, the cost of adding one more component to the infrastructure involves not only the additional cost of hardware, but also the cost of software, plus another server access license, as well as support to make everything work.
Peer–to–peer architecture
With this architecture, all components work together cooperatively, so that there is no single centralized processing unit. All elements of this architecture work together without hierarchy, as shown below:
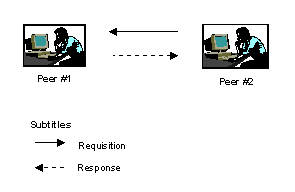
In the case of this architecture, the cost of adding one more component to the infrastructure involves the cost of hardware, plus the cost of software, plus the cost of the support.
The client–server approach will be studied in this article. To provide the reader with a means of comparison, three situations will be reported: two infrastructures based on proprietary software (Novell Netware and Microsoft Network) and one based on proprietary software and free/libre/open software (GLW). The information infrastructure of an imaginary organization called ACME will serve as the installed base. ACME has a single server, 27 clients, offering file sharing, shared access to printers, and access to the Internet.
What is a transaction?
A transaction occurs "when a good or service is transferred across a technologically separable interface. One stage of processing or assembly activity terminates and another begins" (Williamson, 1981). We rarely observe the boundaries of a transaction. We think of a transaction as an isolated operation and we do not think about the details that make a transaction possible and sustainable.
Coase (1960) explains that
"in order to carry out a transaction, it is necessary to discover who it is that one wishes to deal with, to inform people that one wishes to deal and on what terms, to conduct negotiations leading up to a bargain to draw up the contract, to undertake the inspection needed to make sure that the terms of the contract are being observed and so on. These operations are often extremely costly, sufficiently costly at any rate to prevent many transactions that would be carried out in which the price system worked without costs."
Those costs are called "transaction costs." Prochnik (2003) explains that
"transaction costs can be classified as pre– and post–costs to a trasaction. Pre–costs include searching and contractual costs while the post–costs include management and legal costs. Searching costs include those costs for locating and evaluating another party. [...] Contractual costs include those costs for negotiating and writing a contract. [...] Management costs include those for supervising the terms of the contract [...] If these terms are not met, then there are legal costs [...]" [ 1]
We may view most transactions as involving tangible goods. However, computationally, we can also look at transaction costs for information goods (Shapiro and Varian, 1999). For example, Demil and Lecocq note that "dowloading Linux constitutes a transaction" [ 2]. Hence any communication mediated by an information infrastructure constitutes a transaction.
The transaction of communication
"In your brain, each component is very simple, but the interactions between all of these components generate a very complex system. It is akin to the problem that notes that a given set is bigger than its parts. If you take a problem, divide it in half to solve it, you will ignore the need to communicate the solutions in order to solve the whole problem." [ 3]
There are two transactions of communication in the information infrastructure of ACME: the connection transaction, that begins with the user’s authentication (log in) and is maintained until the user leaves the information infrastructure (log out), and the transaction of printing, that starts when any connected user sends data to a printer. For the purposes of this paper, only the connection transaction will be studied.
Novell Network case
When a user enters his username and password, his Windows 98 interface is already modified by Netware (Starlin, 1999), as shown below.
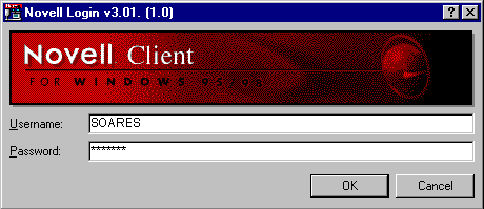
Notice that the system that receives the request is Windows 98, not Novell Netware. The Windows interface sends the request to the Netware client, which in turn sends a request to the Netware server. A positive response from the server means essentially that the user has access to a given information infrastructure.
The Netware server works with one or more Netware clients and runs on a dedicated computer. A Netware client operates on each computer running Windows 98. Netware literally only "talks" to Netware; it is a network operating system [ 4].
So, how do we know how many Netware clients can be attached to a server at a given time? The answer is in the license agreement, which states that:
"Host Software: The software programs provided as part of the Software that are designed to operate on a single computing device, providing access to the shared resources attached to that computer. Host Software may contain technical limitations that limit use of the Host Software to a specified number of computers running the Client Software." [ 5].
For authentication to be approved, a connection to the server will happen only if the number of active connections to it is lower than the "the number of user licenses that You have lawfully purchased or acquired" (Novell, 1998b). The network management software monitors the number of active connections. The license agreement of Netware describes this management software as "Computer programs provided as part of the Software that monitor the number of connections permitted under this License and that are designed to prevent more connections than the number of licensed connections specified by the User Count" [ 6].
If there is any attempt at a connection over the "User Count," the server rejects it. For example, the 28th request for a network connection at ACME, a firm with 27 computers running Windows 98 and Netware clients based on acquisition of 27 user licenses, will be rejected. Netware clients can be installed without limitation, but the number of connections to the server is limited. This limit is fixed by software that provides information on the number of licenses (Starlin, 1999).
Each time comunication between a client and the server takes place, the server management software will be activated to monitor the connection. The CPU of the server is used not to benefit the user, but to monitor the connection. Hence, the user’s hardware is spending time and effort in terms of transaction costs. Attempting to reduce these costs by deactivating the management software in any way is expressly forbidden by the license:
"[...] Property: No title to or ownership of the Software is transferred to You. Novell, or the licensor through which Novell obtained the rights to distribute the Software, owns and retains all title and ownership of intellectual property rights in the Software; including any adaptations or copies of the Softwares. Only the License is purchased to You."
"[...] License Restrictions: Novell reserves all rights not expressly granted to You. Without limiting generality of the foregoing, You may not modify the Connection Management Software to increase the number of connections supported by the Software; use any device, process or computer program in conjunction of the Host Software that increases, either directly or indirectly, the number of connections of the Host Software; reverse engineer, decompile or disassemble the Software, except and only to the extent it is expressly permitted by applicable law; or rent, timeshare or lease the Software unless expressly authorized by Novell in writing. [...]" (Novell, 1998a)
Novell provides licenses in multiples of five in this case [ 7]. In the case of ACME, if ACME needs 27 licenses, it will purchase 30 licenses. Even though the number of licenses is greater than the number of possible active connections, the server will monitor all connections.
Microsoft Network case
The user provides his username, password and domain in a Windows 98 client dialog box, similar to the one below.
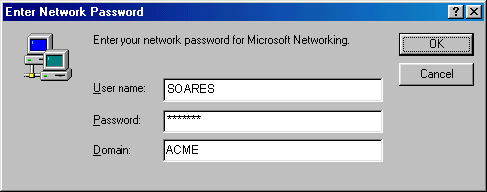
A Windows 98 client sends a request to a Windows server, because in this case it is a remote call. If the response is positive, the user is granted access to the information infrastructure. It is clear that the Windows 98 client and the Server work on different computers and that there is a single Server working with multiple clients. How do we know how many Windows clients can be attached to a server at a given time? To answer that question, we need to look at the architecture of the Microsoft Network.
The Network requires three kinds of licenses: a license for the server, a license for the client and a license for the client to access the server, known as Client Access Licenses (CAL) (Microsoft, 2004a). There are two means of purchasing licenses to a server: per seat or per server.
"With Per Server licensing, each Client Access License is assigned to a particular server and allows one connection to that server for the use of that product. With Per Seat licensing, a Client Access License is assigned to each specific computer that accesses the server" (Microsoft, 2004a).
In our ACME example, the firm has only one server and 27 clients. In this case, Microsoft would recommend the use of Per Server licensing.
"The licensing mode you select depends on which applications you will be using. For example, if you use a Windows NT Server mainly for file and print sharing and on multiple servers, you may be better off with the Per Seat option. However, if you use it as a dedicated Remote Access Server computer, you can select the Per Server concurrent connections option. Use the following guidelines for selecting a licensing mode:
- If you have only one server, select the Per Server option because you can change later to the Per Seat mode.
- If you have multiple servers and the total number of Client Access Licenses across all servers to support the Per Server mode is equal to or greater than the number of computers or workstations, select or convert to the Per Seat option." (Microsoft, 2004a)
A Client Access License must be assigned to each computer which is running a client and connecting with the server.
"Client Access Licenses are separate from the desktop operating system software you use to connect to Microsoft server products. Purchasing Microsoft Windows 95, Windows NT Workstation, or any other desktop operating system (such as Macintosh) that connects to Microsoft server products does not constitute a legal license to connect to those Microsoft server products. In addition to the desktop operating system, Client Access Licenses must also be purchased" (Microsoft, 2004a)
Hence it is necessary to purchase CALs equivalent to the number of potential connections to the server at the same time; in the ACME case, it would be 27 CALs. But what happens if a 28th computer attempts a connection? A mechanism monitoring the number of concurrent connections comes into action and locks out connections to the server, obliging the administrator to interfere and select which connections will be aborted to maintain the integrity of the information infrastructure.
"With Per Server licensing, once the specified limit for concurrent connections is reached, the server returns an error to the client’s computer and does not allow more computer connections to that server. Connections made by administrators are also considered as part of the total number of concurrent connections. When the limit is reached, though, administrators are still allowed to connect to manage the lockout situation. New users, however, cannot connect again until enough users (including administrators) have disconnected to get below the specified limit." (Microsoft, 2004a)
The License Manager is the mechanism that monitors and manages connections to the server (Jennings, 1997). It is clear that each time communication between a client and the server takes place, the License Manager is activated to monitor the connection. Again, transactions costs are being absorbed by the user in a variety of ways, with time and effort spent on network monitoring functions. As might be expected, deactivating the License Manager in any way is expressly forbidden by the license:
"DESCRIPTION OF OTHER RIGHTS AND LIMITATIONS. [...] Limitation on Reverse Engineering, Decompilation, and Disassembly. You may not reverse engineer, decompile, or disassemble the SOFTWARE PRODUCT, except and only to the extent that such activity is expressly permitted by applicable law notwithstanding this limitation." (Microsoft, 2004b)
Hence the server will monitor operations at all times, with incurred transactions costs for all parties involved.
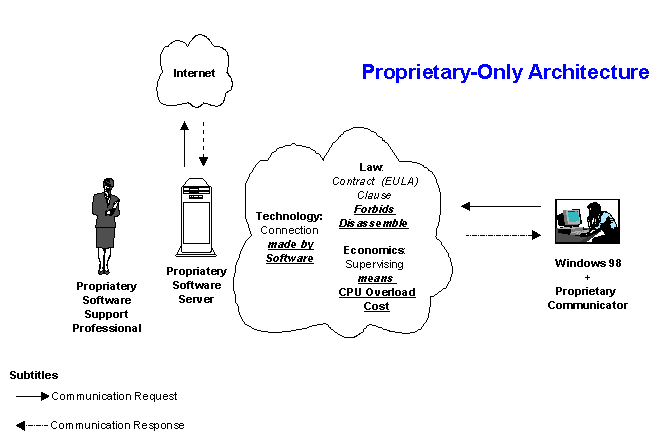
In the two proprietary software cases related above, one notes that law, economics, and technology interfere (Law, 2000) with each other in such a way that contractual obligations do not allow technological modifications allowing the potential reduction of transaction costs for a given customer; see figure below:
GLW architecture case
GLW (GNU/Linux–Windows) allows the use of a GNU/Linux server with Windows proprietary clients. Some of the advantages of GLW are:
- it preserves most of an installed base of Windows devices, without forcing users to drastic changes, reducing the impact of network modification at the user level and instead concentrating it at the administration level;
- it reduces the cost of additional of clients in the installed base;
- it improves the overall information infrastructure of ACME (in our case) by adding the maintainability of free/libre/open source software and its community of users, colaborators, and supporters;
- it takes advantage of the benefits of peer–to–peer computing;
- it reduces the number of formal licenses and contracts monitored by ACME; and,
- it eliminates connection monitoring, reducing transaction costs.
"Samba is a suite of Unix applications that speak the Server Message Block (SMB) protocol. Microsoft Windows operating systems and the OS/2 operating system use SMB to perform client–server networking for file and printer sharing and associated operations. By supporting this protocol, Samba enables computers running Unix to get in on the action, communicating with the same networking protocol as Microsoft Windows and appearing as another Windows system on the network from the perspective of a Windows client." [ 8]
Samba is licensed under the General Public License. It acts as a gateway between the GNU/Linux Server and the Windows clients.
"Samba can help Windows and Unix computers coexist in the same network. However, there are some specific reasons why you might want to set up a Samba server on your network: — You don’t want to pay for — or can’t afford — a full–fledged Windows server, yet you still need the functionality that one provides; the Client Access Licenses (CALs) that Microsoft requires for each Windows client to access a Windows server are unaffordable." [ 9]
The GPL (Free Software Foundation, 1991) obliges that source code is totally accessable and open to modification. Hence, GPL eliminates the problems we noted with proprietary software over modifications. There are no limitations on the number of connections with Samba, merely an issue of network computing capacity; see figure below:
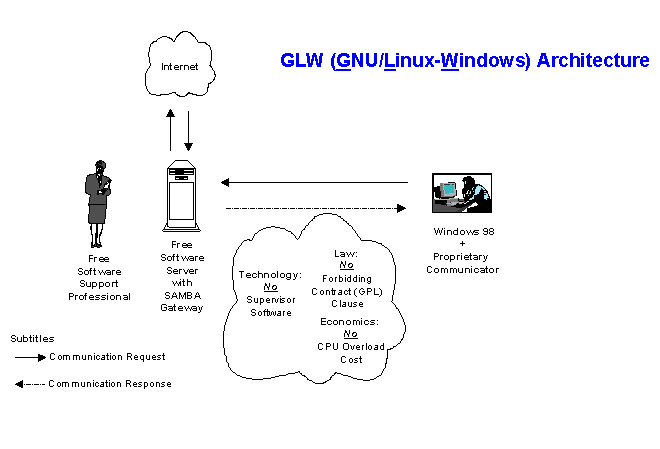
With GLW architecture, Windows clients experience few alterations in the migration to a non–proprietary environment. Hence training costs are minimal. The costs of adding to the installed base are limited to costs of hardware needed, not additional licenses. There may be some costs for GNU/Linux support but direct network software costs, in terms of licenses, are reduced.
Let’s look at each scenario from ACME’s perspective.
With Netware, it would be necessary to license 27 copies of Windows 98 software, plus one copy of the Netware server software, along with 30 licenses for Netware client software. Additionally, there should be a Netware professional to manage it all, which introduces another contract for support.
With Windows, there are 27 copies of Windows 98 software, plus a copy of the Windows server software, plus 27 Client Access Licenses. A Microsoft–trained professional is needed to manage it all.
With GLW, working with GNU/Linux and Windows, ACME will need 27 copies of Windows 98 software, plus a copy of GNU/Linux. There should be a GNU/Linux professional to manage it all.
With Netware and Windows, there are always costs associated with the process of linking a new client to the installed base. These costs are either the cost of an additional client license plus the time and effort of the server to monitor the link or the cost of one more Client Access License.
In the case of GLW, there are no costs associated with the process of linking new clients to the installed base because Samba does not need to monitor the connections, freeing the server to actually work for ACME, and not bother with network policing. Hence, GLW architecture frees the network, and ACME, of a number of transaction costs, in terms of time, effort, and other factors.
Information system costs are largely based on the acquisition of software and hardware and on the training of the personnel to operate the system. Often transaction costs are not completely considered. As information systems grow into information infrastructures, these transactions cost can no longer be ignored.
As we have shown, transaction costs can vary greatly, depending on the kind of software used and its impact on hardware and personnel. We have indicated that there are some considerable savings in transaction costs for computer networks where FLOSS is applied. Further studies will provide more detailed quantative descriptions of the impacts of FLOSS on transaction costs.
Marcus Vinicius Brandão Soares holds a M.Sc. degree in Computing and Systems Engineering from COPPE/UFRJ, Rio de Janeiro, Brazil. He is a member of the Science and Technology Studies research group named NECSO at UFRJ (
www.necso.ufrj.br) and Professor of FLOSS Technology at Estacio de Sá University (
www.estacio.br). He has written for O Globo and ComCiência. His interests include new institutional economics and intellectual property rights and technology.
E–mail: soares [at] marcusvinicius [dot] eti [dot] br
The author would like to thank the people of NECSO for providing the feedback and stimulating conversations; Casey O’Donnell, for his observations on the differences of the prices of licenses and services in emergent and in developed countries; and, Sônia Barroso Brandão Soares for her patience in reviewing the originals.
1. Translation from Prochnik, 2003, p. 12:
"[...] Os custos de transação podem classificados em anteriores e posteriores (ex–ante e ex–post) à realização da transação propriamente dita. Os custos anteriores são os custos de busca e de contratação e os posteriores são os de monitoração e de fazer cumprir o contrato. Os custos de busca abrangem o custo de encontrar e avaliar um parceiro. [...] Os custos de contratação incluem negociar e escrever o contrato. [...] Os custos de monitoração são os custos de fiscalizar o contrato, observando seu cumprimento pelo parceiro. [...] Por último, os custos de fazer cumprir o contrato são os custos de implantar uma solução quando o contrato não está sendo seguido. [...] Ao nvel da economia nacional, entre os custos de transações, estão todos os gastos com advogados, contadores, bancos, mensuração da qualidade, comércio e seguros. [...]"
2. Demil and Lecocq, 2003, p. 10.
3. Translation from Torvalds and Diamond, 2001, p. 126:
"Pense no seu cérebro. Cada peça é simples, porém as interações entre as peças geram um sistema muito mais complexo. É aquele problema que diz que o conjunto é maior do que as partes. Se você pegar um problema, dividi–lo pelo meio e disser que as partes são complicadas pela metade, estará ignorando o fato de que é preciso acrescentar a comunicação entre as duas metades."
4. Soares, (1995, p. 423) explains that
"[...] quando surgiram as redes, os computadores, antes funcionando isoladamente, já possuam seus respectivos sistemas operacionais locais — SOL. Portanto, uma premissa básica do software introduzido para fornecer os novos serviços foi perturbar o menos possvel o ambiente local, principalmente a interface que esse ambiente ofereceria a seus usuários. Neste contexto surgiram os sistemas operacionais de redes (SOR) como uma extensão dos sistemas operacionais locais complementando–os com o conjunto de funções básicas, e de uso geral, necessárias à operação das estações, de forma a tornar transparente o uso dos recursos compartilhados [...]. Dentre as funções do sistema operacional de redes destaca–se, assim, o gerenciamento do acesso ao sistema de comunicações e, conseqüentemente, s estações remotas para utilização de recursos de hardware e software remotos. [...]"
or in translation: "[...] when networks appeared, computers, that worked in an isolate manner before, already had their local operating systems — LOS. Hence, a basic starting point of the software introduced was the possibility of offering new services as to disturbing the local environment as little as possible, mainly the interface that this environment offered to the users. In this context the network operating systems (NOS) broke up as an extension of the local operating systems, complementing them with the set of basic functions, and of general use, necessary to the operation of the stations, to make the use of shared resources seem transparent to the user [...] Among the functions of the network operating system one can accentuate the management of the access to the comunication system and, consequently, to the use of hardware and software of the remote stations [...]"
7. Novell provides other licensing agreements over specific periods of time and with other conditions. These sorts of agreements are outside the scope of this paper. For more details, see www.novell.com/licensing.
Grady Booch, James Rumbaugh, and Ivar Jacobson, 1999. The unified modeling language user guide. Reading, Mass.: Addison–Wesley.
Ronald H. Coase, 1960. "The problem of social cost," Journal of Law and Economics, volume 3, pp. 1–44, at http://www.sfu.ca/~allen/CoaseJLE1960.pdf. accessed 21 September 2004.
Benoit Demil and Xavier Lecocq, 2003. "Neither market nor hierarchy or network: The emerging bazaar governance," at http://opensource.mit.edu/papers/demillecocq.pdf. accessed 21 September 2004.
Free Software Foundation, 1991. "GNU General Public License, Version 2 (June), " at http://www.gnu.org/licenses/gpl.txt. accessed 21 September 2004.
Chris Gane and Trish Sarson, 1983. Análise Estruturada de Sistemas. Rio de Janeiro: LTC.
Ole Hanseth, 2002. "From systems and tools to networks and infrastructures — From design to cultivation. Towards a theory of ICT solutions and its design methodology implications," at http://heim.ifi.uio.no/~oleha/Publications/ib_ISR_3rd_resubm2.html. accessed 21 September 2004.
Roger Jennings, 1997. Usando Windows NT Server 4 — O Guia de Referência Mais Completo. Fourth edition. Rio de Janeiro: Campus, 1997.
John Law, 2000. "Economics as interference," at http://www.comp.lancs.ac.uk/sociology/papers/law-economics-as-interference.pdf. accessed 21 September 2004.
Microsoft, 2004a. "Licensing and License Manager," at http://www.microsoft.com/resources/documentation/windowsnt/4/server/proddocs/en-us/concept/xcp12.mspx. accessed 21 September 2004.
Microsoft, 2004b. "NT Server End User License Agreement," at http://proprietary.clendons.co.nz/licenses/eula/windowsntserver-eula.htm. accessed 21 September 2004.
Novell, 1998a. Netware 5.0 Server Communication Version 5 Manual. Provo, Utah: Novell.
Novell, 1998b. Netware 5.0 Software License and Limited Warranty. Provo, Utah: Novell.
Meilir Page–Jones, 1988. Projeto Estruturado de Sistemas. São Paulo: McGraw–Hill.V. Prochnik, 2003. Economia dos Contratos — Princípios da Teoria dos Custos de Transação. Rio de Janeiro: Instituto de Economia — UFRJ.
Carl Shapiro and Hal R. Varian, 1999. Economia da Informação — Como os Princípios Econômicos de Aplicam à Era da Internet. Sixth edition. Translation by Ricardo Inojosa. Rio de Janeiro: Campus.
G. Starlin, 1999. Netware 5 Completo — Manual do Administrador CNE. Second edition. Rio de Janeiro: Book Express.
Linus Torvalds and David Diamond 2001. Só Por Prazer — Linux: Os Bastidores da sua Criação. Translation by Flávia Beatriz Rssler. Rio de Janeiro: Campus.
Jay Ts, Robert Eckstein, and David Collier-Brown, 2003. Using Samba. Second edition. Sebastopol, Calif.: O’Reilly.
Oliver E. Williamson, 1985. The economic institutions of capitalism: Firms, markets, relational contracting. New York: Free Press.
Paper received 12 October 2004; accepted 3 November 2004.


Copyright ©2004, First Monday
Copyright ©2004, by Marcus Vinicius Brandão Soares
Reducing transaction costs in information infrastructures using FLOSS by Marcus Vinicius Brandão Soares
First Monday, volume 9, number 11 (November 2004),
URL: http://firstmonday.org/issues/issue9_11/soares/index.html