

This paper provides a thorough analysis of the mainstream media representation of hackers, hacking, hacktivism, and cyberterrorism. The intensified U.S. debate on the security of cyberspace after September 11, 2001, has negatively influenced the movement of online political activism, which is now forced to defend itself against being labeled by the authorities as a form of cyberterrorism. However, these socially or politically progressive activities often remain unknown to the public, or if reported, they are presented in a negative light in the mass media.In support of that claim, I analyze five major U.S. newspapers in a one–year period with 9–11 in the middle. I argue that certain online activities are appropriated for the goals of the political and corporate elite with the help of the mass media under their control to serve as pretext for interventions to preserve the status quo. Thus, the media portrayal of hacking becomes part of the elite’s hegemony to form a popular consensus in a way that supports the elite’s crusade under different pretexts to eradicate hacking, an activity that may potentially threaten the dominant order.
Contents
Research description
Article–level analysis
Sentence–level analysis
Cyberactivism
Cyberterrorism
From cyberactivism to cyberterrorism
Conclusion
Research description
This research project can be conceptualized as a two–level analysis of newspaper articles that mention hackers or the act of hacking. For each identified article that contained some version of the word "hack," I conducted the evaluation on the article level, paying special attention to the theme and framing of the story, as well as on the sentence level. For this latter, I used KWIC analysis, that is, a keyword–in–context type of content analysis. I looked at the particular form of the word "hack," the attributes associated with this word, and other nouns mentioned along with it.
After careful consideration I chose five daily U.S. newspapers for analysis [ 1]: the New York Times (owned by the New York Times Company), the Wall Street Journal (owned by the Dow Jones & Company), the Washington Post (owned by the Washington Post company), the San Jose Mercury News (owned by Knight Ridder), and USA Today (owned by Gannet Co.). All of these parent companies have a significant network of other media outlets, especially the latter two. These five newspapers should provide a fairly wide overview of the American print media landscape, especially the mainstream version. Combined, they reach approximately 6.3 million readers daily. On Sundays, their combined circulation reaches over seven million.
I believe these figures give a fair ground for generalization. Furthermore, each one of them adds a unique taste to the mix. The New York Times is the largest daily newspaper with a very strong international perspective, regarded as the most prestigious nationwide paper with a leading agenda–setting role. The Wall Street Journal, the paper of the business elite with a corporate viewpoint, is also based in the financial capital of the United States, and also is known for quality technology reporting. Given its physical location, the Washington Post has a close proximity to the federal government; therefore, it is probably more sensitive to government affairs. The San Jose Mercury News is a viable alternative to these East Coast papers. It is located in Silicon Valley, thus its strength is in technology coverage. It is smaller in size, yet well known for breaking stories the previous establishment papers might have avoided. Finally, the USA Today covers the remaining landscape as a truly national chain newspaper.
The collection of the relevant articles was carried out through Lexis Nexis, Academic Elite (also known as Lexis Nexis Light), and ProQuest. The New York Times, Washington Post, and USA Today articles were fully accessible through Academic Elite. For complete results, Wall Street Journal articles were collected from ProQuest, while San Jose Mercury News reports were obtained from the full version of Lexis Nexis.
After many experiments I found that the optimal search phrase, which is wide enough to cast the needed results, but narrow enough to yield a manageable number of hits, would be this one:
(Internet OR "World Wide Web" OR online) AND hack! [2]
Henceforth, I decided that I would only look at articles that contain some variety of the word "hack"; that is, my research would focus on how U.S. daily newspapers use the concept of hacking, hackers, or even hacktivism. Finding enough of these reports would also provide a rich sample of data to evaluate the context in which they appear. I also decided that cyberactivism and cyberterrorism should be the subject of a smaller, separate project — to be discussed at the end of this chapter — since many articles dealing with these two topics may not contain the word "hack."
Originally, I wanted to look at a year’s range of articles. The start date of 1 January 2001, seemed to be a good choice. The majority of the research was completed in March–July 2002. Thus, the exact period I used in the research ran from 1 January 2001, through 21 March 2002. For parts of the analysis specific to the change of discourse as a result of the events of September 11, however, I moved the beginning of the period ahead to 4 March 2001, so 9–11 would fall exactly in the middle of the period (191 days before and after) and would, therefore, yield a more balanced and objective picture.
After the first round of data collection, I found nearly 1,100 articles in the five newspapers that contained some variant of the word hack. Then I eliminated irrelevant articles, such as ones with the "wrong" words (e.g., hackles, hackney or hacksaw), with names (e.g., Hackman, Hackensack, or Hacker–Asperger), and compound words that did not directly refer to either the act or the perpetrators of hacking (e.g., hacker tongue, hacker creation, or hacker–oriented magazine). In addition, book or film review articles and sentences in illustration captions were ignored. Eventually, I came up with 627 relevant articles, and 1,552 relevant sentences within them for the analysis.
Article–level analysis
The most frequent form of the word hack* was hacker or hackers (74 percent).
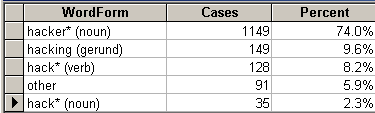
Table 1: Distribution of forms of the word "hack."
During the analysis, I categorized all articles according to their main and sub-themes. The main theme was decided according to the framing of hacking or hackers mentioned in the article:
- Hackers: if the article was primarily about a hacker or hackers
- Hacking incident: if the article primarily reported an incident or incidents
- Online security: if the article was generally about computer vulnerabilities, protection about those vulnerabilities, or the possibility of security breaches
- National security: if the vulnerability or security was projected as significant to national security or implied military or other government–level response
- Cybercrime: if the article presented the hacking or hacker(s) in the crime/law enforcement context
- Other: if the article could not be classified under any of the above
According to this categorization, the distribution of main themes were as follows:
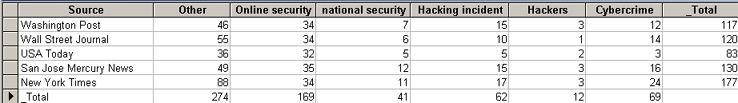
Table 2: Thematic distribution of focus articles.
As shown by the data above, online security themes proved to be the most popular among the identified ones across the various sources. It should come as no surprise, since online security issues underlie all forms of hacking (its antithesis, if you like) and national security issues concerning cyberspace. The New York Times seemed to have given slightly more attention to hacking incidents, national security issues, and cybercrime. In fact, the larger amount of stories is expected from a paper with a generally wider net for catching news. The other apparent trend is the smaller figures for USA Today stories on hacking and hackers, which again can be explained by the same news net size; in this case, a smaller net with larger holes (meaning that a daily newspaper covering the entire United States will inevitably be more superficial and selective).
For our purposes, a more telling figure would be the distribution of these articles by theme in regards to September 11. These data below use the adjusted time period that contains 9–11 right in the middle.
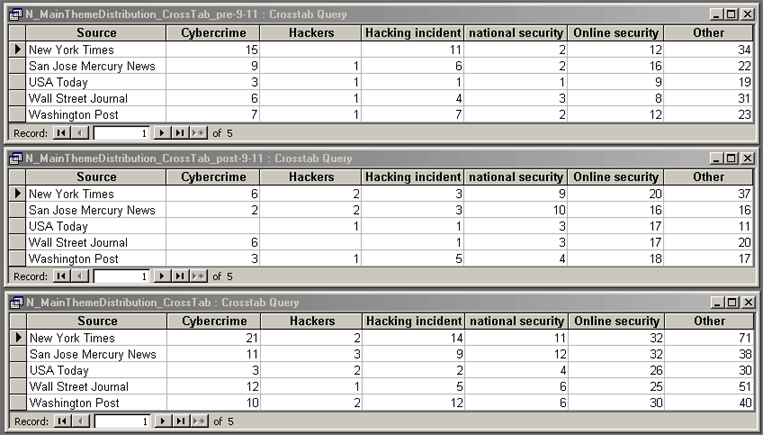
Table 3: Thematic distribution of focus articles pre– and post–September 11.
The upper two thirds contain the numbers before and after 9–11, while the bottom third has the totals. It is immediately apparent that the framing of these articles as cybercrime decreased, while articles on national security and online security increased. Stories on hackers slightly increased (except for the Wall Street Journal). Other interesting changes include the fivefold increase of San Jose Mercury News articles on national security, and the increased attention to online security, but no change for cybercrime themes in the Wall Street Journal. The reason is probably the Journal’s business orientation, which makes cybercrime committed against companies and online retailers a particular interest.
Apart from the changing discourse and newspaper attention to these topics, there is another important factor affecting these data. Namely, the number of actual hacking incidents, hacktivist campaigns, and online criminal activity decreased. It is mainly because hackers (including crackers, script kiddies, hobby hackers, hacktivists, and others) basically gave a break to the government and corporations following September 11. In the time of national tragedy, grief, and worldwide sympathy, hackers and hacker groups suspended their activities, many offline and online demonstrations were canceled or postponed, and even alldas.org, the most popular defacement archive, stopped registering hacks. Generally, out of sympathy or patriotism, criticism of the United States, its federal government, or corporate America was put on hold.
The following graph indicates the distribution of newspaper articles of which a hacking incident is the main theme. (The triangles on the bottom line indicate the events by date, drawn from the newspapers reports on them. The five lines above it — in different colors — show the distribution of reports by newspaper source.)
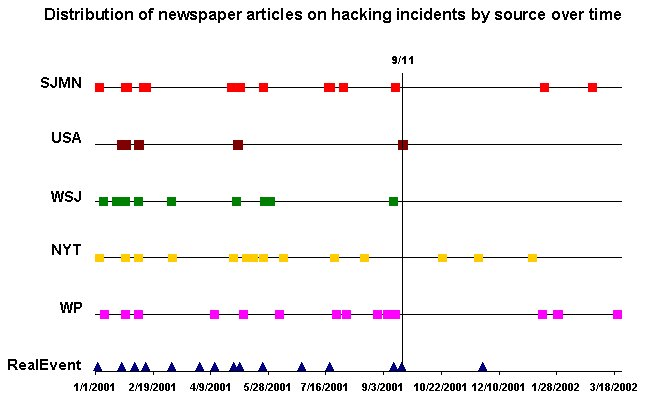
Figure 1: Distribution of newspaper articles on hacking incidents by source over time.
In fact, during the course of this analysis, I identified 57 relevant real–life events that generated most of the reporting. I call them the newsmakers:
1/2/2001 Coolio pleads guilty 1/3/2001 AOL IM 1/3/2001 EBay down for hours 1/11/2001 Los Alamos hacker arrested 1/15/2001 Music copyright protection and DMCA hack report 1/18/2001 Mafiaboy pleads guilty 1/23–26/2001 Microsoft down for three days 1/30/2001 Router bug revealed 2/3/2001 Davos hack (reported worldwide 2/6) 2/5/2001 Wireless WEP bug revealed 2/12/2001 Kournikova hits 2/14/2001 Kournikova creator OnTheFly turns himself in 2/14/2001 Windows XP released 3/6/2001 Bibliofind revels hacks 3/9/2001 FBI report of Russian credit card thefts 3/21/2001 FBI warning of cyberattacks 3/30/2001 DoubleClick reveals hacks 3/30/2001 Microsoft warns Explorer bug 4/13/2001 Report on cyberspace spilloff of U.S.–China spyplane incident 4/15/2001 U.S. tax deadline v4/24/2001 FBI arrests two Russian hackers 4/26/2001 FBI warning of Chinese hacker strike 4/29/2001 U.S.–China hacker war erupts 5/4/2001 Whitehouse.gov attack 5/23/2001 CERT attack 5/24/2001 Attrition.org announces closure 6/4/2001 Windows Messenger announced 6/19/2001 Mafiaboy trial 6/27/2001 Storm Cloud operation report 7/11/2001 Napster shutdown order 7/15/2001 Privacy concerns over Microsoft Passport 7/16/2001 Sklyarov arrested 7/19/2001 Code Red attacks WhiteHouse.gov 7/31/2001 Code Red return warned by FBI 8/3/2001 Wireless bug discovered 8/5/2001 SANS advisory on Code Red II 8/30/2001 Hotmail vulnerability revealed by hack 9/4/2001 Microsoft Passport closed because of vulnerability 9/11/2001 WTC attacks 9/12/2001 Mafiaboy sentencing 9/18/2001 Nimda hits 10/9/2001 Richard Clark appointed Cyber–Tsar 10/30/2001 First steganography report 11/3/2001 Microsoft acknowledges Passport vulnerability 11/26/2001 Badtrans hits 12/5/2001 Indian Trust Fund report 12/12/2001 DrinkOrDie software piracy operation report 12/20/2001 Microsoft warning of XP vulnerabilities 12/22/2001 NIPC warning on XP vulnerabilities 1/2/2002 AOL IM bug revealed 1/4/2002 FBI endorses XP patch 1/18/2002 Mafiaboy pleads guilty 2/1/2002 WEF hacktivism prediction 2/11/2002 BlackIce vulnerability revealed 2/12/2002 SNMP vulnerability revealed 2/28/2002 NYT hack and vulnerability revealed Table 4: List of relevant "newsmaking" events.
Among these events, eleven proved to be the big newsmakers with the largest number of articles generated. Finally, this different graph includes the top five big long–term newsmakers related to hacking.
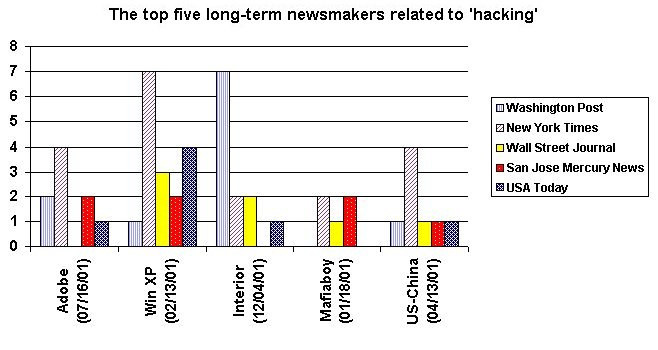
Figure 2: Distribution of the top five "long–term newsmakers."
This graph provides a better opportunity to see which newspaper pays how much attention to which events among these top five newsmakers. They are as follows:
- Adobe: Russian programmer Dmitry Sklyarov arrested in Las Vegas after he arrived to a hacker conference to present a paper on the vulnerabilities of Adobe’s E–Book. He broke the protection code of Adobe’s E–Book Reader, which his company then sold commercially. His act was not illegal under Russian law. He was the first one accused in the U.S. under the new Digital Millennium Copyright Act.
- XP: Microsoft announced and later released its new operating system, Windows XP. It has generated a lot of coverage because of its vulnerabilities and privacy issues.
- Interior: A judge ordered the shutdown of the Internet site of the Department of Interior’s Bureau of Indian Affairs after an investigation (including a white–hat hack) found that its computer system could be hacked and would compromise Indian Trust Funds. (After September 11, the Department of Interior made it once again into the news because of potentially sensitive information found and consequently ordered to be removed from the Web site of the National Park Service.)
- Mafiaboy: Young Canadian hacker arrested for DoS and hack attacks against Yahoo!, eBay and other major Web sites. The media covered the trial from the plea to the sentencing, and finally the jailing of the youngster.
- U.S.–China: Chinese hackers pledged to launch a large–scale attacks against U.S. Web sites in retaliation for the death of a Chinese pilot who was killed after his plane collided with a U.S. spy plane along the Chinese border. This "Hack the USA Week" also coincided with other relevant dates, like 1 May, the workers’ day, 4 May, day of the youth, and 8 May, the two–year anniversary of the accidental NATO bombing of the Chinese Embassy in Belgrade. The media covered the event from the early FBI/NIPC (National Infrastructure Protection Center) warnings to the U.S. counter–attack by patriotic hackers and the eventual truce declared by Chinese hackers.
According to these findings, the Sklyarov incident was reported in all newspapers, except the Wall Street Journal, which — again — may have avoided using the word hack or hacker. Stories on hacking and Windows XP were also reported across the board, with the least attention by the Washington Post. On the other hand, the Post predictably seemed to be a lot more interested in reports on the computer vulnerabilities of the Interior Department. Reports on Mafiaboy and the U.S.–China cyberskirmish appeared in all newspapers, but again with multiple stories in the New York Times and minimal attention by the Washington Post.
One specific type of stories, warning articles, call attention to a specific threat, vulnerability, or virus attack. The information contained therein can best be extracted if we plot it on a chart by the specific types of warning (again, each line represents a specific source, in order from the bottom upward: Washington Post, New York Times, Wall Street Journal, USA Today, and San Jose Mercury News):
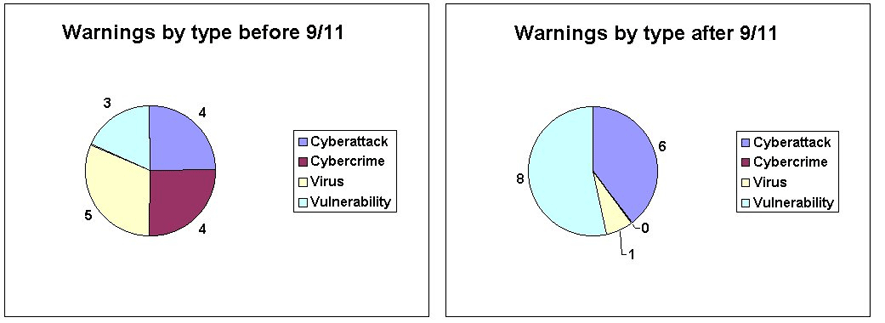
Figure 3: Distribution of "warning" articles over time by type of warning.
It is visible from this chart that cybercrime warnings fall exclusively in the first few months of 2001, while vulnerability warnings increased in the last few months of 2001. In addition, cyberattack warnings are concentrated around the U.S.–China cyber conflict in May 2001 and around the weeks following September 11. If we compare this chart with the one that groups these warnings by the type of entity that issued them (below), it is apparent that there are more warnings after September 11 by corporations and non–governmental organizations. It can be explained by the changed political climate, that is, more organizations feel the need to warn the public once vulnerabilities are found, and similarly, more corporations seem to be willing to reveal vulnerabilities in their products or servers, even if they compromise trust and public image.
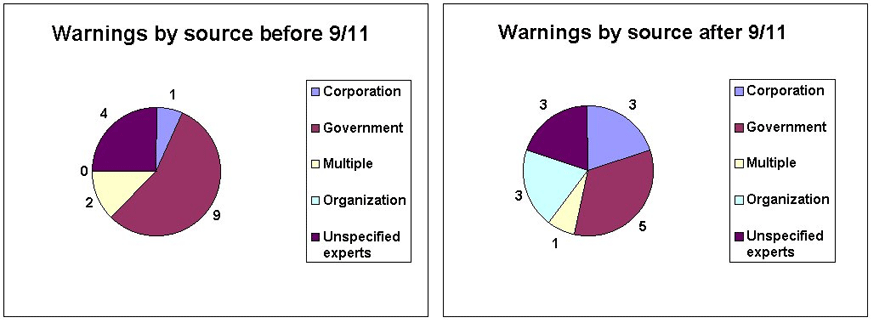
Figure 4: Distribution of "warning" articles over time by source of warning.
Sentence–level analysis
Apart from what context hackers and hacking are represented in, the most valuable information comes from the analysis of the actual sentences in which the word hack* appears. I coded 1,552 sentences that contained some variant of "hack." I looked at the nouns that co–occurred with hack, hacking, and hackers, as well as the adjectives and verbs associated with hackers. I also considered how their image based on these findings changed after September 11.
First, it should be considered that many of these reports are actually about hacking incidents that never happened, that is, what hackers could do or could have done. This tendency is demonstrated by the fact that almost 10 percent of all sentences examined are in the conditional tense. Even more interestingly, the ratio of conditional tense for sentences with hacking or hackers mentioned in them increased more than twofold: 30.4 percent before, and 69.6 percent after September 11.
The apparent motivation of hackers was also coded, according to how the act was framed in the sentence. I realize that the motivations presented are rather dependent on the context (framing), since what is activism for one may be terrorism for another, or what is classic hacking for one, a criminal activity for another. Thus, I examined the framing of the article (versus the actual motivations possibly revealed on the sentence level). Classic hacking contains, for example, anti–copyright activities (but not for further sale of the hacked or cracked product), or anything that defies authority. For the authorities, of course, these are all criminal acts. Similarly, a politically motivated hacking act falls under activism, while it could be framed by the target as an online security breach, or by the authorities as crime or even as terrorism threatening national security.
In an attempt to cover all possible motivations, I have come up with nine different categories: classic, activism, criminal, online security, terrorism, espionage, other, unspecified, or not applicable. It is understood that this categorization builds a great deal upon subjective decisions, therefore, it mirrors just as much my interpretation of the author’s intentions as it does the author’s interpretation of the hacker’s intentions. In other words, these numbers cannot be generalized, yet they show one important fact: the majority of reports lack any reference to the possible motivations of hackers.
Furthermore, it seems that hacking incidents are mostly recognized if they serve political activism or criminal goals. This is understandable, since it is indeed the goal of hacktivists to identify their acts as such, just like criminal activity is defined so upon the very nature of goals aimed or achieved. It also follows, however, that the distinction between terrorist, classic, or other types of hacking remains difficult.
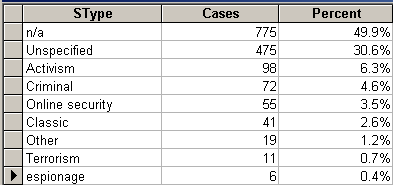
Table 5: Types of hacking in the focus articles.
The following table shows the distribution of indicated motivations for each newspaper before and after 9–11. The numbers demonstrate that hacking framed as activism and criminal activity clearly decreased following September 11, while the online security and terrorism angles slightly increased.
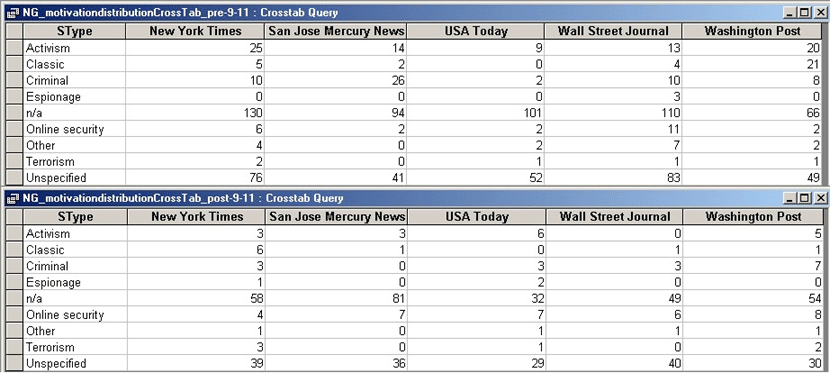
Table 6: Distribution of focus articles by motivation pre– and post-September 11.
In order to get a better picture of how the media perceive hackers, I looked at all the other subjects that occurred together with hackers in the same sentence. I separated them in two groups. In the first one, I put the subjects that were simply listed together with hackers (e.g., "hackers and spies do everything from stealing credit card numbers to sending out political propaganda"). The second group had subjects that were used to refer to hackers or used as a synonym for them (e.g., "terrorists or other hackers could disrupt everything"). These subjects were then rated according to whether they are positive (assigned 1) or negative (assigned –1) words. Positive words included socially accepted attributes or qualities, such as a "clever writer of software code" or "highly skilled programmers." Negative words or phrases were just the opposite, such as "digital vandal" or "malicious outsider." The remaining words, such as neutral (e.g., "computer people"), mixed (e.g., "ragtag renegades, sought–after professionals") were assigned a 0.
In line with my hypothesis, the average rating for hackers based on how they were referred to in newspapers became more negative after September 11.
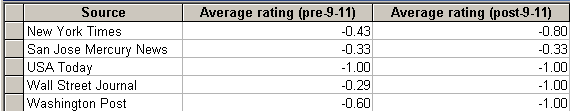
Table 7: Image of hackers before and after September 11 based on direct references.
Similarly, the average rating for hackers based on what other subjects were mentioned together in the same sentence did worsen after September 11, except for the Wall Street Journal, which moved upwards, although not significantly.
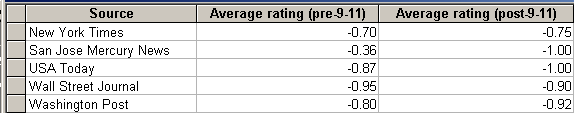
Table 8: Image of hackers before and after September 11 based on co–listed subjects.
I also examined the attributes (mostly adjectives and prefixes in noun phrases) that occurred together with hackers. These were evaluated according to their generally positive, negative, or neutral meanings, and averaged for the periods before and after 9–11. Consistently with previous findings, the ratings decreased following the terrorist attacks for three out of the five newspapers. Only USA Today seemed to achieve some noticeable improvement in their use of attributes for hackers [ 3].
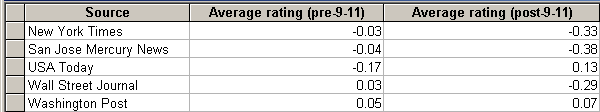
Table 9: Image of hackers before and after September 11 based on pre–fix attributes.
In terms of the acts most frequently associated with hackers, the table below shows — in decreasing order — the verbs that most often occurred together with hackers [ 4].
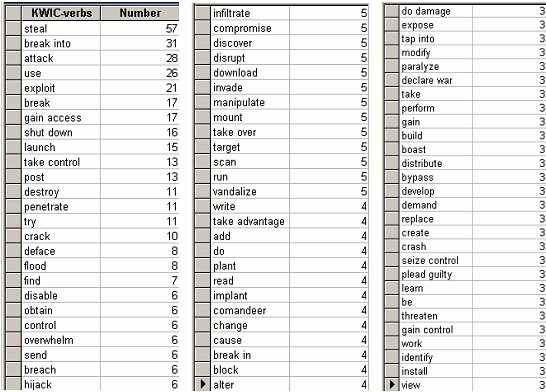
Table 10: List of verbs associated with hackers.
For a better understanding of what hackers do — according to newspaper reports — I grouped these verbs into types of actions that best represent the nature of that activity. So, for example, "gain access," "enter," "breach," "break into," etc., were collected under the heading Access Computer(s), while "steal," "compromise," "download," "obtain," etc., were summed under Extort Information. While some of these categories seem to overlap, I attempted to devise them so that the verbs — based on their specific context in the sentence if in doubt — would fit best in only one category.
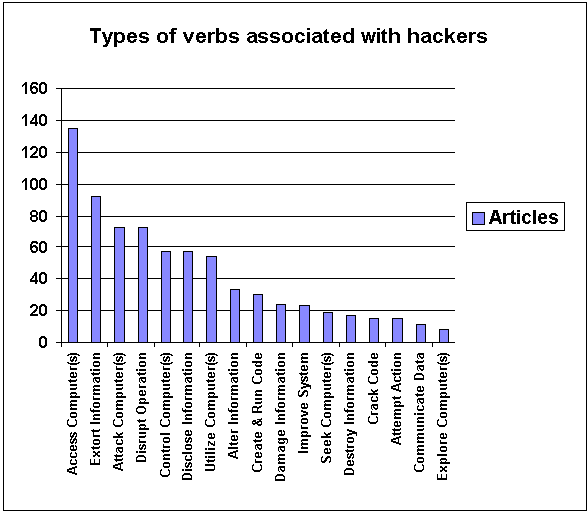
Figure 5: Distribution of verb groups associated with hackers.
As evident, the main activity most often associated with hackers is accessing computers, followed by extorting information (crime) and attacking computers and disrupting operations (terrorism), which points directly to the media’s interpretation of hacking as illegal intrusion into computer systems in order to steal data, disrupt its operations, or destroy information. It stands in sharp contrast with the hackers’ own conception of their activity such as exploring and seeking computers, cracking code, communication data, and improving systems, all of which appear at the low end of the frequency scale.
Cyberactivism
To collect the relevant articles from the same pool of newspapers and for the same time period for cyberactivism was even more difficult. I experimented with several key phrases and eventually combined the results from multiple searches. For an article to make it into the result list it had to have the word activist or activism or some variation occur together in the same sentence with the word Internet or its main variations. Therefore, a keyword phrase looked like this:
(activis** w/s (Internet OR cyber OR online))
Certainly, I used other variations of the words, like protest* for activism, and cyber* or "World Wide Web" for the Internet [ 5]. Still, the number of false positives was overwhelming. After careful reading of all returned documents, I closed in on 19 related articles in the target five newspapers. Altogether, they had 99 cited sources, all of which were also coded.
Between January 2001 and March 2002, there were seven politically charged hacking incidents that gained significant media attention. In two cases, no particular event or cause could be determined that prompted the act of hacktivism. The other cases were distributed between two types of articles: one about the political activism itself, of which hacking was a part, and one about profiling the protesters.
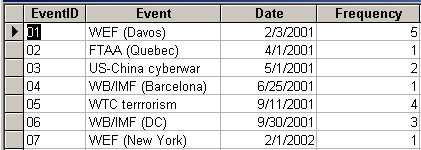
Table 11: List of relevant protests.
A good part of political activism incidents are related to the worldwide anti–globalization movement. These protests are organized in conjunction with the annual meetings of the main international financial and trade organizations. There is an increasing tendency for reliance on the Internet on the protesters’ part for not only organization and mobilization purposes, but also for disrupting the meetings using online tools.
In early February 2001, the World Economic Forum (WEF) met in Davos, Switzerland. As the relevant San Jose Mercury News article noted, "The Internet has turned out to be a remarkable tool for non–violent protest on a scale activists could only dream of before" (Koppel, 2001). Indeed, beyond the organizational and mobilization tasks, the Internet was used in at least two fairly novel ways. Internet users from all over the world could log into a Web site where they sent political messages to the conference participants, which messages then were automatically projected onto a hillside in a large size. The other way was a hack into the WEF online database, from which the perpetrators allegedly took credit card numbers and travel itineraries of conference participants. However, the WEF insisted that the actual motivation or affiliation of the perpetrators had not been determined.
The hack was reported by a Swiss daily. The San Jose Mercury News article mentioned above was rather negative in its treatment of the Davos hacktivists. The paper even managed to have the editor of the Toronto–based Hacktivist magazine condemn this particular form of hacktivism, namely the extortion of confidential data. Reporting on the same incident, USA Today consequently shifted focus to online security. The Wall Street Journal article was short and hegemonic; it reported the incident basically from the WEF’s point of view, quoting only the WEF spokesman and mentioning imminent court action without detailing the possible motivations. It stands in sharp contrast to the Washington Post article on the same topic, which was considerably longer and more analytical.
The Davos hack — if indeed committed by online activists — signaled a new tactic in the repertoire of protesters: extortion of personal and private data from secured databases. Whereas the obtained information has apparently not been used, a fact that confirms the non–criminal nature of the incident, it shifted the focus to privacy issues, which definitely did not help voicing the activists’ cause, yet granted them headline status.
One year later, the WEF met in New York. Some activists said in articles that appeared before the protests that there had been no online action in the planning. The Electronic Disturbance Theatre, on the other hand, said that they were preparing for cyberattacks against the WEF site. A leader of EDT called it a "Net Strike," pointing out that it aimed at "social disturbance" rather than disruption or destruction, as feared by the authorities. The Davos hack from a year before was indeed referred to in the article. It must be mentioned, however, that no online action and only a very moderate street protest were reported after the meetings.
FTAA’s meetings (in the beginning of April 2001 in Quebec) were accompanied by large–scale protests by anti–globalization activists as well as laborers’ unions and umbrella organizations of workers, affected by NAFTA policies. The Washington Post printed a longer piece profiling the protesters who were attending the demonstrations from the Washington area. They mentioned eight sources on the side of the activists, most of them university students in Washington. The article did devote a few paragraphs to the views of the protesters.
Belonging to the same anti–globalization protest wave, one of the largest demonstrations was planned to coincide with the Annual Meetings of the World Bank and the International Monetary Fund in Washington, D.C., scheduled for the end of September. The meetings were called off after September 11, and the protests were scaled down and shifted to an anti–war agenda. Because of the planned scale of the demonstrations, the media started to pay attention a month in advance. On 5 September, the Washington Post published a positively toned article on the protesters, citing as many as nine named sources, all supporting the activists. The affiliation of these people covered all major types, including U.S. business, U.S. NGO, academic, foreign citizen, and unspecified. On the other end, only two unnamed sources were mentioned: the law enforcement agencies and WB officials in general and only once. No direct action use of the Internet was mentioned; it only served "as their bulletin board, telephone and door–to–door fundraiser" (Fernandez, 2001). Prompted by the preparations for this event, two related articles were published in the Wall Street Journal. The first one looked fairly balanced in its list of cited sources; however, the whole article was framed with a story of a successful police infiltration among the lines of protesters preparing for action against the 2000 Republican Convention in Philadelphia. The other one was on video activism in the anti–WTO protests on the same day, with similarly balanced citations. What is striking about these two articles on online political activism is that both were published on the very September 11, the morning hours of which brought terror to America. It was somehow symbolic, a prelude to the marriage of terrorism and activism.
The first article in the target newspapers after 9–11 that mentions online political activism came out on September 21 in the New York Times (Harmon, 2001). It was a piece about the opponents of the War on Terrorism, citing eight named sources, all of them activist. This article was quickly answered by another NTY report two days later on cyberspace as a potential battleground, with thirteen cited sources, all of them taking side with the powers (Schwartz, 2001). The whole article was framed as a warning about cyberattacks as retribution for the War on Terrorism. They admitted that there were no real professional hacker terrorists yet, but they also said that it was only a matter of time when the "convergence of bad guys and good stuff occurs" (Schwartz, 2001). Another source pointed out that cyberterrorism was likely to be only an amplification of a traditional attack (more plausible). He considered the tools used as weapons of mass disruption.
Reacting to the actions of the Dispatchers, a new hacker group formed specifically to commit online sabotage against Middle Eastern countries suspected to have sponsored the terrorist attacks, the USA Today gave account of the incidents, citing five experts on the topic, four of them speaking out against the hacktivists, more specifically the group’s founder, Hackah Jack (Graham, 2001). Interestingly, two of these cited sources would normally be expected to speak out on behalf of the resistance, like the German Chaos Computer Club, and the Electronic Frontier Foundation. However, this way the article achieves a unified view that condemns hacktivism from both sides.
The blurring of hacktivism and terrorism really occurred when Hackah Jack stated that their goal was "to cripple the USA’s enemies by stripping away their computer access ... and if you cripple the Net in that country, that will cripple them as well" (Graham, 2001). One wonders how defacing Web sites really achieves that goal.
This article brings up the U.S.–China hacker incident that happened earlier that year. It was widely reported across the media. The whole idea of an all–out international "hacker war" between two powers really caught the imagination of a few journalists. Consider, for example, the opening paragraph in the New York Times, which called it the first hacker war:
"It was a Big Hack Attack, a harbinger of World Wide Web War I, with ‘zombies’ throwing ‘worms,’ Chinese patriots invoking the ultimate sacrifice and American teenagers giving electronic Bronx cheers." (Smith, 2001)Now compare this tone with the opening sentence in the USA Today:
"Several government Web sites were off–line Tuesday after being attacked by hackers possibly reacting to recent tensions between the United States and China." (Kessler, 2001)This is more like an objective and informative account of the events, undoubtedly less intriguing, though. Later in the first article, the author continues the sensationalist and colorful language:
"The worst attacks were coordinated assaults from computer servers commandeered by Chinese hackers, who used them as ‘zombies,’ in hacker parlance, to send disruptive signals or even e–mails poisoned with the vicious viruses called worms." (Smith, 2001)While the appeal of the NYT article was in its language, the USA Today article remained one–sided by only citing sources identifying with traditional seats of power. Quite predictably, the official reaction de–emphasized why the hacking incidents occurred; instead they focused on how to defend against similar attacks:
"Instead of concentrating on the political motivation of hackers, security experts say that the real problem is that most computer systems are not secure, and software flaws make it easier for hackers." (Kessler, 2001)At this point, the article switched the discourse to online security, which is quite typical and understandable in case of hacking incident reports. The author also connected it with the Israel–Palestine conflict, which seemed to be a legitimate juxtaposition, even though the nature of the real–world conflicts is very different.
As the author points out, the reporting of hacking incidents is also in the interest of security software makers, which then can build marketing campaigns upon them. Thus, these firms will also lobby the media to report hacking activity. This is one of those rare occasions when the interest of corporations actually coincides with that of online activists aspiring for publicity.
The only online activism reported in this period where I could not immediately identify a particular offline incident to which the hacking was connected was the large–scale attacks against Microsoft servers in late January 2001. The incident was not prompted by any real–life event; the motivation was most likely Microsoft’s traditional position as the de facto representative of a monopolistic corporation and proprietary code. Being an IT company, Microsoft is a favorite target for hackers who favor open source and community development, as well as free resources.
These two articles in the Washington Post and USA Today both overwhelmingly cited sources in favor of the status quo. The reports connected the incident to earlier DoS attacks against the Web sites of eBay, Yahoo, CNN, and Amazon, as well as to the case of the Canadian underage hacker, Mafiaboy, who had just pleaded guilty of hacking.
On the whole, it seems that when the report is about a hacking incident, mainly sources supporting power and the status quo are cited. Activists are only heard when an article is about profiling them. The role and view of hacktivism changed after September 11. When the nation as a whole is under threat or attack from a foreign enemy, domestic criticism of the political leadership on other issues becomes limited. Furthermore, it seems to be in the interest of the administration to keep up this condition of threat on national security in order to keep domestic opposition contained.
Cyberterrorism
In this smaller project, I looked at articles that mentioned cyberterrorism. Given the focus of the larger research on hackers and hacking, I conducted a less comprehensive data collection than in the other projects, and only used Lexis–Nexis for this search. Therefore, the results were limited to only four newspapers (the five focus papers, excluding the San Jose Mercury News); even among those, one had a limited availability pool within the database (Wall Street Journal). In the research, I was seeking news reports that mentioned terrorism or terrorists together with the Internet in the same sentence. A sample search phrase would look like this:
terroris! w/s Internet
I immediately found that the number of hits was more than what could be handled. There were approximately 660 articles altogether in four of the five target newspapers for the roughly one year period of which 9–11 fell exactly in the middle. What is informative, however, is that about 640 of them (97 percent) were published after September 11. I further experimented with the search phrase to find that if the two terms were required to be within five words of each other, the result was about 270 hits, 95 percent of which were post-9–11. Looking for the exact phrase "cyberterrorism," I found only 31 occurrences, 24 (77 percent) of which came after 9–11. Finally, I also looked at hacker(s) occurring together in the same sentence with terrorists or terrorism (hacker! w/s terroris!) only to locate 17 articles before and six after September 11.
These findings are confirmed with a visual representation of the occurrences of these articles on a time scale (please note that this data now contain all five newspapers in their full availability). As opposed to the limited search for the same key phrase, this one resulted in 59 relevant articles (the same numbers above, plus six more for the Journal and seven for the San Jose Mercury News).
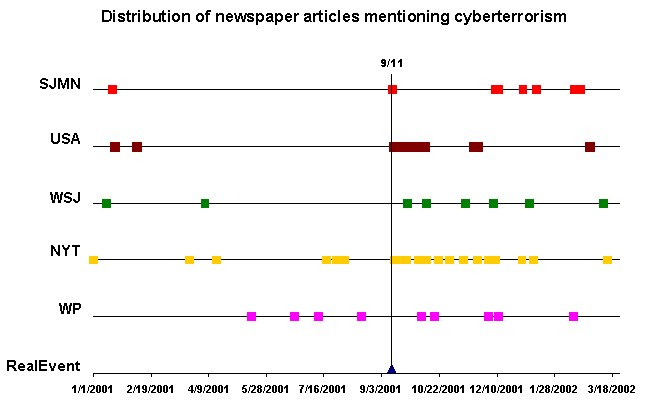
Figure 6: Distribution of focus articles mentioning cyberterrorism.
As evident from the graph above, as well as from the table containing the pre–, and post–9–11 numbers, the discourse on cyberterrorism increased tremendously following the terrorist attacks. Since no real cyberterrorist attacks have yet occurred, it is safe to say that the main issue here is the possibility of a future cyberattack by terrorists, a topic that gives ample opportunity for manipulating public opinion and influence policy makers in directions that the apparent threat may not even justify.
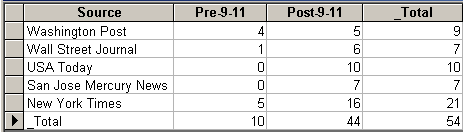
Table 12: Distribution of cyberterrorism articles pre- and post–September 11.
From cyberactivism to cyberterrorism
The attitude that is fueled by the changing discourse and is the result of media reports blurring the boundaries of cyberactivism and cyberterrorism is truly reflected in the statement by Virginia Governor James S. Gilmore (2001) in his testimony before the House Committee on Science: "Prior to September 11, many people questioned whether nation–states or rogue terrorists had the capability to disrupt our critical infrastructures on a wide scale. Since September 11, we must presume they do." He also proclaimed that "the threat is higher than before September 11" (National Infrastructure Protection Center, 2001). It is especially important when one tries to understand the current governmental mindset echoed by the news media, which relies increasingly on official reports. The administration now operates under the assumption that terrorists are capable of wide–scale cyberattacks; they are actively seeking opportunities to strike, and hackers — possessing the very technical knowledge necessary to hack into systems — also may have the motive. Furthermore, the perceived threat of cyberattacks is deemed higher because of the horrific 9–11 hijackings. Through government warnings and media reports, this perception transforms into fact in the public mind, even when the Internet had only as much to do with 9–11 as the roads the terrorist took to drive to the airport, or the phone they used to call for a cab.
One impact of the 9–11 terrorist attacks and the much–discussed vulnerability of the American cyberspace was the birth of the potential "terrorist hacker," as referred to by one newspaper. In many cases, hackers and terrorists are mentioned together in the same sentence. It can be argued that — in spite of their separation — simply mentioning them in the same article connects them in the public mind. For example:
"Last year a report by the General Accounting Office, an internal government watchdog, found weaknesses in the computer network that could allow terrorists or hackers to ‘severely damage or disrupt national defense or vital public operations or steal sensitive data.’" (Williams, 2001)But newspapers go beyond just simply mentioning the two together; sometimes they actually do classify hackers as terrorists and hacking as cyberterrorism, as shown by the next two examples (interestingly, all three quoted articles are by staff writers at the Washington Post):
"By taking out certain data networks, he said, another country, terrorists or other hackers could disrupt everything from telecommunications and the power grid to hospitals and banking." (Cha, 2001)"The growth is being spurred partly by federal agencies’ need to ward off acts of cyberterrorism, such as hacking, from their top–secret networks." (Webb, 2001)
Sometimes, blurring the boundaries between hackers and terrorists occurs more subtly. Consider, for example, the following quote from the Washington correspondent for USA Today:
"The same hackers trying to break into corporate computers also might try to infect a satellite with viruses that could instruct it to shut down or change its orbit." (Stone, 2001)This assumption is not only unfounded, but also dangerous. It is clear that doing such an act could only be a goal for a terrorists, therefore, it is again implied that "corporate hackers" are, indeed, a small step away from terrorists.
As an example for blurring the boundaries between cyberactivism and cyberterrorism, consider two articles on the very same event, namely, the announcement that the Annual Meetings of the IMF/World Bank in Barcelona will instead be held online:
"Protest groups have warned that they are planning to sabotage the virtual conference with a campaign of cyber–terrorism that will be just as disruptive as their violent marches." (Riley, 2001)"[...] that they possess all the cyber weapons necessary to hack into the conference and shut it down." (Riley, 2001)
"A spokesman for the World Bank said that any acts of cyber terrorism next week would reflect badly on the anti–globalisation groups, particularly ‘their attitude towards free speech and freedom of discussion.’" (Riley, 2001)
Sneaking cyberterrorism into the text is certainly detrimental to the image and cause of the activists and legitimizes law enforcement response or pre–emptive action — on a scale equivalent to a true cyberterrorist act, e.g., aimed at destroying lives through damaging electronic systems — before the protesters’ voice could be heard. Now, consider what the spokesperson really said, as reported in another paper:
"If the protesters succeed in disrupting the conference, ‘that will reflect badly on them and their attitude towards free speech and freedom of discussion.’" (Vidal and Denny, 2001)This author apparently struggled with identifying the online protesters, calling one of them a "protester/hacker who specializes in IT protests," but at least he avoided labeling them as terrorists. A closer look at the sentence uttered by the author of the previous article reveals an interesting contradiction: "... any acts of cyber terrorism would reflect badly on the [anti–globalisation groups’] ... attitude towards free speech and freedom of discussion" (Riley, 2001). Would a cyberterrorists really worry about their attitude toward free speech?
Along the same dichotomy, consider, for example, these two quotes from the New York Times. The first one — appearing in an article before September 11 — describes hacktivism in an objective manner:
"Socially conscious organizations are increasingly engaged in a practice known as hacktivism. Hacktivists use computer hacker tactics to advance their causes. For instance, they organize virtual sit–ins, which can paralyze a targeted site by flooding it with requests for information." (Mirapaul, 2001)The second one — published after September 11 — gives a more negative view of the same activity:
"Malicious hactivists in the past have downloaded potentially sensitive information from India’s Bhabha Atomic Research Center and stolen credit–card numbers from a database belonging to the American Israel Public Affairs Committee, a powerful pro–Israel lobby." (Puzzanghera and Ackerman, 2001)
Conclusion
In conclusion, I have found the following trends in the newspaper articles I examined:
- The discourse is shifting from hackers as criminals to hackers as cyberterrorists.
- There is a larger focus on cyberterrorism now, even if it has not yet happened.
- The language of the media blurs the differences between hacktivism and cyberterrorism.
- Motivations are not discussed in news articles about hacking, except when the article is about profiling hackers.
- Articles on hackers and hacking increasingly use sensationalist tone and language.
One main consequence of media reporting is that online political activism is distorted as a disruptive act by cyber–vandals, hackers, or potential cyberterrorists. It negatively affects public opinion, which results in favorable conditions for passing laws and regulations that limit this alternative way of advocacy and political protest.
About the author
Sandor Vegh received his Ph.D. from the University of Maryland in 2003. His dissertation deals with the Internet’s impact on democracy and democratization, control and resistance power struggle in cyberspace; more specifically online political activism (hacktivism), and the mass media’s role in the process.
E–mail: veghs [at] fulbrightweb [dot] org
Notes
1. The collection of the relevant articles was carried out through Lexis Nexis, Academic Elite (also known as Lexis Nexis Light), and ProQuest. The New York Times, Washington Post, and USA Today articles were fully accessible through Academic Elite. I conducted control queries for these three papers from their own online search engines and found that the result list did not differ from the Academic Elite list significantly. Since it was not the case for the Wall Street Journal, those articles were collected in a separate search from ProQuest. The San Jose Mercury News reports were obtained from the full version of Lexis Nexis.
2. Certainly, the exact search phrase depended on the particular database used (e.g., hack! or hack* or hack?).
3. In fact, the apparent increase in image is due to one single article in November 2001 that looked at the impact of the USA PATRIOT Act on hackers. The piece by John Yaukey leans toward the hackers’ side, since the two sources used are from the hacker group Cult of the Dead Cow and the NGO Center for Technology and Democracy — both are critical of the USA PATRIOT Act. It must also be mentioned that this article had been written a few months before Yaukey was hired as the new national security and defense correspondent at the Washington bureau of the Gannett News Service.
4. This table includes those verbs that occurred at least three times in the 1,552 sentences examined.
5. Again, the exact syntax of the search phrase depended on the actual electronic database used. Also, ProQuest did not have the w/s (within sentence) feature, so there I used w/20 (within 20 words).
References
A.E. Cha, 2001. "For Clarke, a career of expecting the worst; newly appointed cyberspace security czar aims to prevent ‘Digital Pearl Harbor’," Washington Post (4 November).
A. Fernandez, 2001. "Varied Paths; One Goal: Taming Global Capitalism; Diverse Protesters Unite Against IMF, World Bank," Washington Post (5 September).
J.S. Gilmore, 2001. "Testimony," Committee on Science, U.S. House of Representatives, Congress of the United States. Washington, D.C. (17 October).
J. Graham, 2001. "Computer pros launch hack attack on Mideast," USA Today (19 September).
A. Harmon, 2001. "Demonstrators find that the Web is a powerful tool," New York Times (21 November).
M. Kessler, 2001. "China troubles linked to attacks on Web sites run by U.S. government," USA Today (2 May).
N. Koppel, 2001. "Anti–globalist protesters make point as hackers; Internet a tool for non–violent activists," San Jose Mercury News (11 February).
M. Mirapaul, 2001. "A stronger, more theatrical role for female activists," New York Times (23 July).
National Infrastructure Protection Center (NIPC), 2001. Cyber protests related to the war on terrorism: The current threat. (November). Washington, D.C.: National Infrastructure Protection Center, at http://www.nipc.gov/publications/nipcpub/cyberprotests1101.pdf, accessed 31 December 2004.
J. Puzzanghera and E. Ackerman, 2001. "U.S. networks run big risk of cyber–strikes, experts assert," San Jose Mercury News (1 October), p. 1A.
M. Riley, 2001. Anti–globalisation battle shifts into cyberspace, The Age (Australia) (22 June), at http://www.theage.com.au/news/national/2001/06/22/FFXUZ11F7OC.html, accessed 9 July 2002; also at http://www.theexperiment.org/articles.php?news_id=1389, accessed 31 December 2004.
J. Schwartz, 2001. "Cyberspace seen as potential battleground," New York Times (23 November), p. 5B.
C.S. Smith, 2001. "The first world hacker war," New York Times (13 May), p. 2.
A. Stone, 2001. "USA’s dependence on satellites places nation at risk. ‘Militarization of space’ controversial, perhaps inevitable," USA Today (11 January).
J. Vidal and C. Denny, 2001. "Cyber war declared on World Bank," Guardian (London) (20 June), at http://www.commondreams.org/headlines01/0620-02.htm, accessed 9 July 2002.
C.L. Webb, 2001. "CACI Profit Surged 58% in Quarter; Government Work Lifts Tech Firm," Washington Post (17 August).
K. Williams, 2001. "U.S. seeks to build secure online network; Telecom firms asked for help in constructing private ‘Govnet’ system," Washington Post (11 October), p. A10.
Editorial history
Paper received 2 November 2004; accepted 30 December 2004.


Copyright ©2005, Sandor Vegh All Rights Reserved.
The media’s portrayal of hacking, hackers, and hacktivism before and after September 11 by Sandor Vegh
First Monday, volume 10, number 2 (February 2005),
URL: http://firstmonday.org/issues/issue10_2/vegh/index.html